What you will need
- VPS IP address, login (usually root or a user with sudo), SSH port (default is 22).
- SSH client:
- Windows 10/11: built-in OpenSSH in Windows Terminal / PowerShell / CMD (recommended) or PuTTY.
- macOS / Linux: pre-installed ssh in Terminal.
Option A — quick connection using a password (Windows/macOS/Linux)
Command (replace user and 1.2.3.4 with your own values):
ssh user@1.2.3.4 -p 22
When you log in for the first time, confirm the host key (yes), then enter your password.
Basic client and authentication options are described in the OpenSSH manual.
Option B — Key-based protection (recommended)
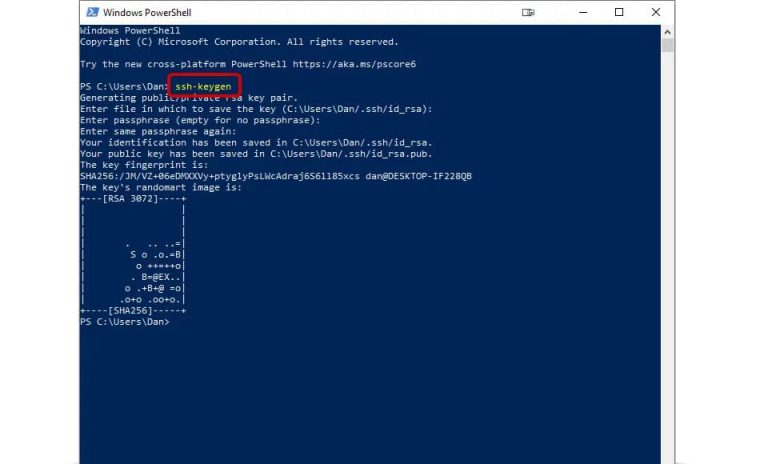
Step 1. Generate a key pair on your PC
In Windows 10/11, open PowerShell and run:
ssh-keygen -t ed25519 -C “my-comment”
# if ed25519 is not available:
# ssh-keygen -t rsa -b 4096 -C “my-comment”
The keys will appear in C:\Users\<name>\.ssh\ (or ~/.ssh on macOS/Linux): private — without extension (keep secret), public — .pub (copy it to the server).
Details on generating keys in Windows: Microsoft/phoenixNAP/HowToGeek.
Step 2. Upload the public key to the server
Method 2.1 — automatically (if password access is available):
ssh-copy-id -i ~/.ssh/id_ed25519.pub user@1.2.3.4
The utility will add the key to ~/.ssh/authorized_keys and set the permissions.
Method 2.2 — manually (via password login):
ssh user@1.2.3.4
mkdir -p ~/.ssh && chmod 700 ~/.ssh
nano ~/.ssh/authorized_keys
# paste the contents of your .pub here, then save
chmod 600 ~/.ssh/authorized_keys
Don’t get confused: only .pub goes to the server; we never copy the private key. Permissions .ssh = 700, authorized_keys = 600 (otherwise you will get Permission denied (publickey)).
Step 3. Connect using the key
ssh -i ~/.ssh/id_ed25519 user@1.2.3.4
To avoid entering the parameters each time, add the profile to ~/.ssh/config:
Host myvps
HostName 1.2.3.4
User user
Port 22
IdentityFile ~/.ssh/id_ed25519
Now, ssh myvps is sufficient. Documentation on ssh_config (all key parameters — Host, User, Port, IdentityFile).
Option C — via PuTTY (Windows), if GUI is more convenient
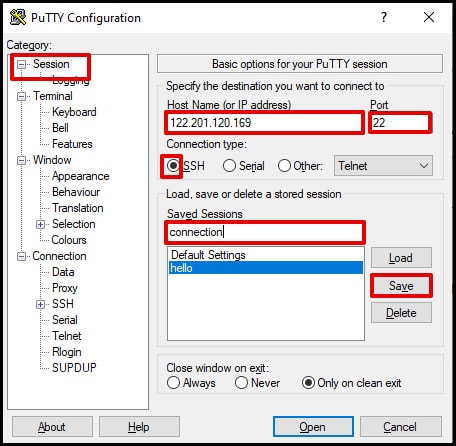
- Download and run PuTTY → Session tab → specify Host Name (IP/domain), Port=22, Connection type=SSH → Saved Sessions → Save → Open.
2. If you are logging in with a key: PuTTYgen → upload your private key or create a new one → save in .ppk format, then in PuTTY: Connection → SSH → Auth → Private key file for authentication — select .ppk.
3. (Optional) Log in to the session and save the profile so you don’t have to enter the parameters every time.
Verification and basic configuration
Check the availability of port 22 from your PC:
# Linux/macOS:
nc -vz 1.2.3.4 22
# Windows (PowerShell):
Test-NetConnection 1.2.3.4 -Port 22
Permission denied (publickey) → check:
- whether the public key (.pub) has been transferred to the server,
- the permissions for ~/.ssh (700) and authorized_keys (600),
- whether IdentityFile matches locally.
Enhancing server security (after configuring keys)
Open /etc/ssh/sshd_config and check (or add) the lines, then restart sshd:
# prohibit direct root login (recommended)
PermitRootLogin no
# prohibit passwords, leave only keys
PasswordAuthentication no
PubkeyAuthentication yes
# (optional) non-standard port:
# Port 2222
sudo systemctl restart sshd
Supported key directives and algorithms are described on the man page sshd_config/ssh_config.
Copying files
SCP:
scp -P 22 file.zip user@1.2.3.4:/home/user/
SFTP (interactive):
sftp -P 22 user@1.2.3.4
(Both methods are included in the OpenSSH client package.)


