What we do and why
- We don’t work under root — we create an administrator with sudo.
- Login only with SSH keys, passwords are disabled.
- We enable UFW: “everything is closed except what is necessary.”
- We install Fail2Ban: it blocks IPs when selecting a password/key.
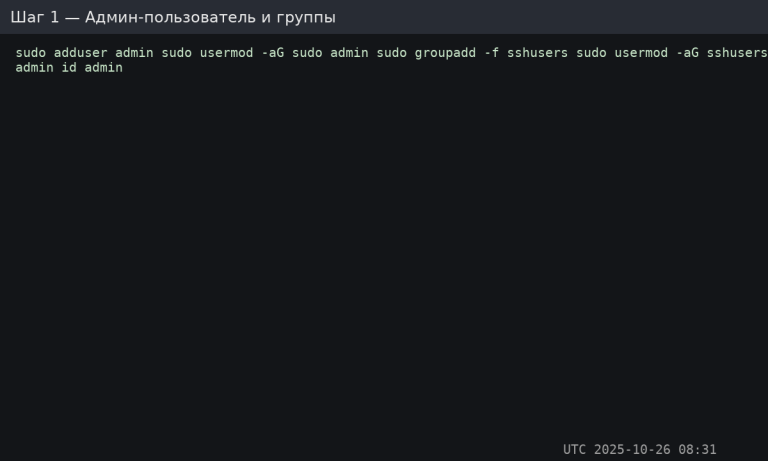
Admin user and groups
We create a user and add them to sudo + the restrictive SSH group:
sudo adduser admin
sudo usermod -aG sudo admin
sudo groupadd -f sshusers
sudo usermod -aG sshusers admin
id admin
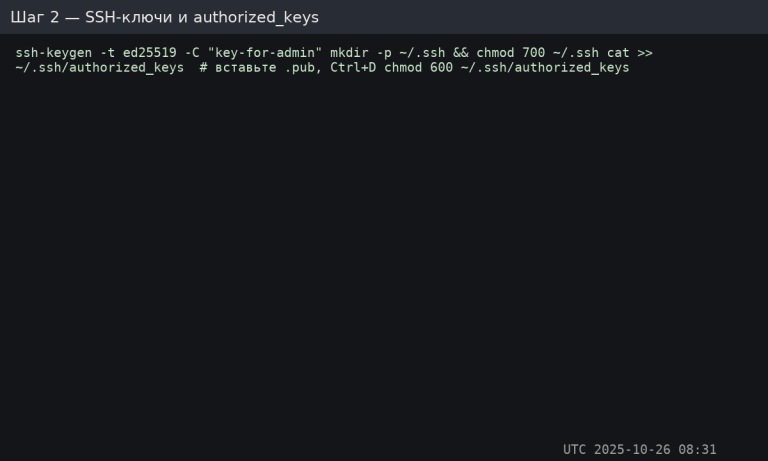
SSH keys: generating and adding
Locally (Windows/macOS/Linux):
ssh-keygen -t ed25519 -C "key-for-admin"
On the server as root or an existing administrator:
sudo -u admin -H bash -lc 'mkdir -p ~/.ssh && chmod 700 ~/.ssh'
sudo -u admin -H bash -lc 'cat >> ~/.ssh/authorized_keys' # insert content *.pub, затем Ctrl+D
sudo -u admin -H bash -lc 'chmod 600 ~/.ssh/authorized_keys'
Important: only the public .pub key is sent to the server. The private key is stored locally.
Strengthening SSH (disabling passwords and root login)
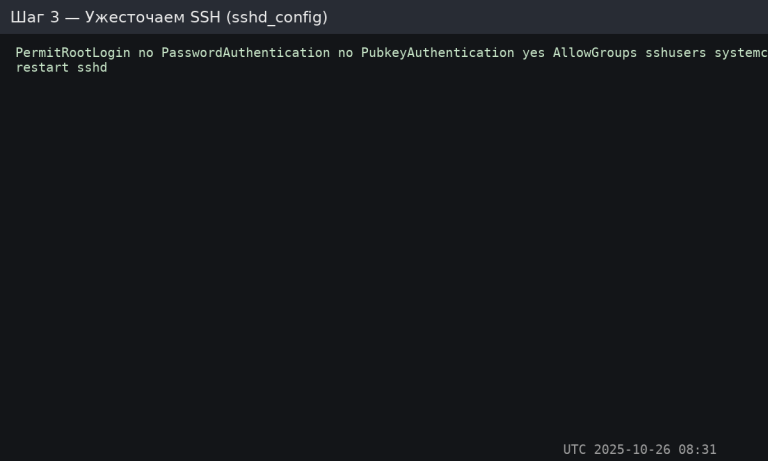
Open /etc/ssh/sshd_config and specify:
PermitRootLogin no
PasswordAuthentication no
PubkeyAuthentication yes
AllowGroups sshusers
Restart SSH:
sudo systemctl restart sshd
Verify that the keys work before disabling passwords, otherwise you will lose access.
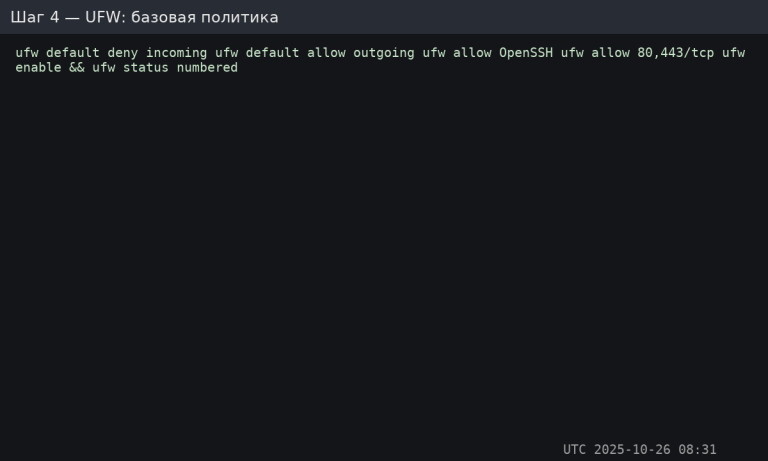
UFW: “closed by default”
sudo ufw default deny incoming
sudo ufw default allow outgoing
sudo ufw allow OpenSSH # port 22
sudo ufw allow 80,443/tcp # if you need a website
sudo ufw enable
sudo ufw status numbered
Need additional ports (e.g., 8080)? Add an explicit rule: sudo ufw allow 8080/tcp.
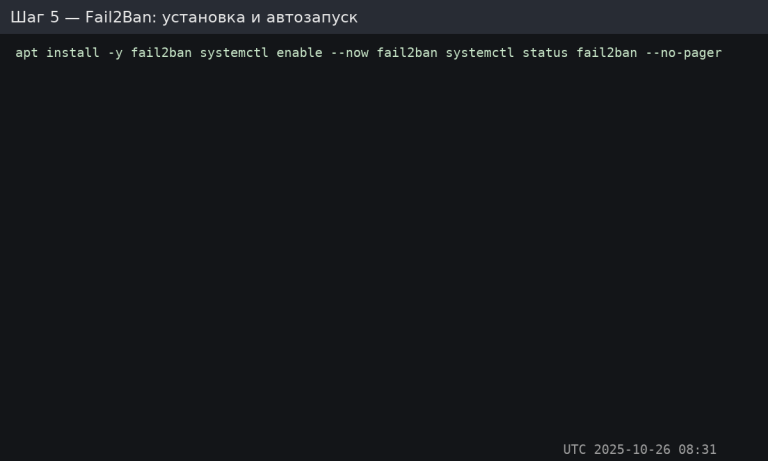
Fail2Ban: installation and autostart
sudo apt -y install fail2ban
sudo systemctl enable --now fail2ban
sudo systemctl status fail2ban --no-pager
Fail2Ban configuration: jail.local for sshd
Create/edit
/etc/fail2ban/jail.local:
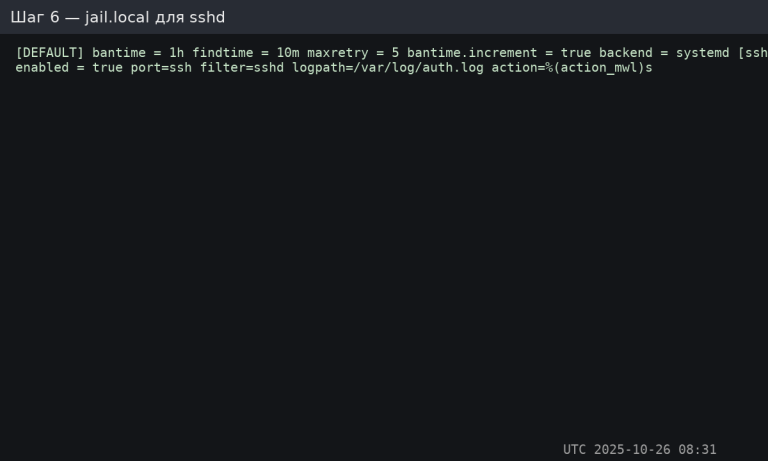
[DEFAULT]
bantime = 1h
findtime = 10m
maxretry = 5
backend = systemd
bantime.increment = true
[sshd]
enabled = true
port = ssh
filter = sshd
logpath = /var/log/auth.log
action = %(action_mwl)s
Restart:
sudo systemctl restart fail2ban
%(action_mwl)s will send an email (if email is configured) + log, and also block the IP.
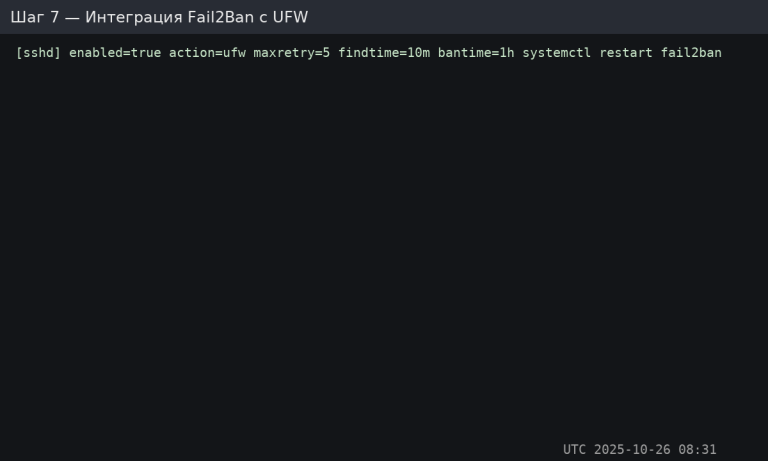
Integrating Fail2Ban with UFW (alternative)
Create a file
/etc/fail2ban/jail.d/ufw-sshd.local:
[sshd]
enabled = true
action = ufw
maxretry = 5
findtime = 10m
bantime = 1h
Apply:
sudo systemctl restart fail2ban
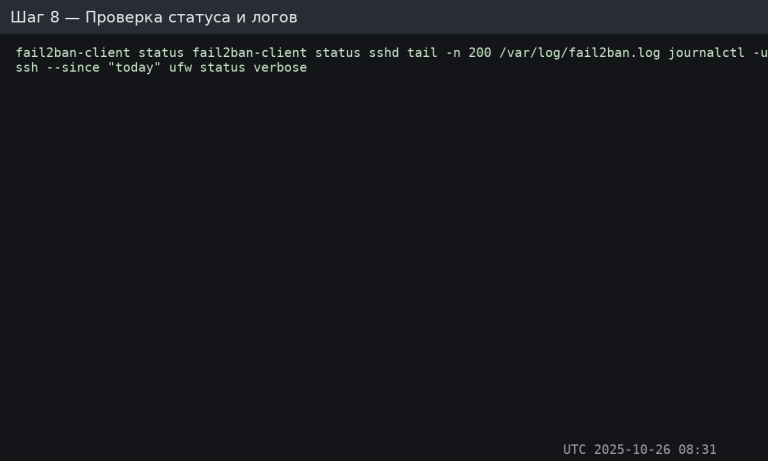
Checking operation and logs
sudo fail2ban-client status
sudo fail2ban-client status sshd
sudo tail -n 200 /var/log/fail2ban.log
sudo journalctl -u ssh --since "today"
sudo ufw status verbose
How to test the ban: from another node, make 5–6 incorrect login attempts, check the sshd status — the IP will appear in the list of blocked IPs.
Security bonuses (optional)
- Change the SSH port (not a security measure, but reduces scanner noise): Port 2222 in sshd_config + ufw allow 2222/tcp.
- Restrict SFTP access (chroot) for the group.
- Enable 2FA for SSH: libpam-google-authenticator + configuration of /etc/pam.d/sshd and sshd_config (AuthenticationMethods publickey,keyboard-interactive).
- Limit sudo attempts: passwd -l root, sudo visudo with timestamp_timeout=5.
Security checklist
- Key-based login works, passwords and root login are disabled.
- UFW: deny incoming/allow outgoing, only necessary ports are allowed.
- Fail2Ban protects sshd (and optionally nginx/postfix/…); logs are checked.
- Test ban is performed, rules and accesses are documented.